Introduction
SSH multi-hopping, also known as SSH tunneling through multiple hosts, is a technique that involves creating an SSH connection through one or more intermediate hosts before reaching the final destination. This approach is often used in situations where direct SSH access to the final destination is not possible due to network restrictions, security policies, or other reasons.
How It Works
- Initial Connection: You start by SSH-ing into the first host (the “jump host”).
- Tunneling Through Intermediate Hosts: From the first host, you then SSH into the next host in the chain, and so on, until you reach your final destination.
- End-to-End Encryption: Each step of the way, the SSH protocol encrypts your connection, ensuring that your data is protected as it travels through each host.
Command Syntax
SSH multi-hopping can be achieved in several ways, such as using the -J option in SSH, chaining SSH commands, or using a combination of the -L and -t options for more complex scenarios.
Benefits
- Enhanced Security: Multi-hopping can add an extra layer of security. Since each hop is encrypted, it becomes more difficult for an attacker to intercept or tamper with the data.
- Bypass Network Restrictions: It allows you to connect to a target network or host that isn’t directly accessible from your current network, which is useful in tightly controlled network environments.
- Simplified Access Management: Instead of opening up many hosts to direct SSH access, you can limit access to a few jump hosts. This simplifies access control and can improve overall network security.
- Privacy and Anonymity: By hopping through multiple hosts, it becomes more difficult to trace back the connection to its original source, offering a degree of anonymity.
Use Cases
- Accessing a secure network: For instance, accessing a server in a private network from an external network.
- Bypassing firewalls or NAT: When direct access to a host is blocked by a firewall or NAT (Network Address Translation).
- Managing multiple layers of a network architecture: Useful in complex network architectures where different layers of the network are segmented and isolated for security purposes.
Risks and Considerations
- Complexity: The setup can become complex and difficult to manage, especially with many hops.
- Latency: Each hop introduces additional latency, which can impact performance.
- Security of Intermediate Hosts: The security of the tunnel is only as strong as the security of the weakest host in the chain.
Creating and Using SSH Keys in Windows
Generating SSH keys with OpenSSH (Windows 10 and newer)
For Windows 10 only
- Open the Windows 10 Start menu and search for “Apps & Features”. In the “Apps & Features” heading, click “Optional Features”.
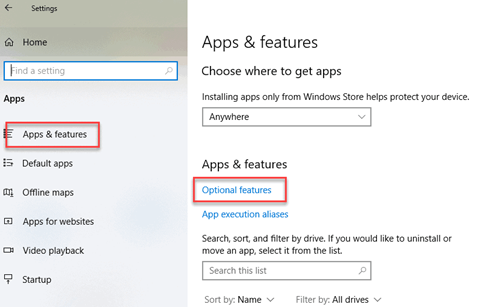
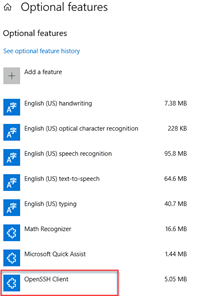
- Scroll down the list to see if “OpenSSH Client” is listed. If not, click the plus sign next to “Add a feature”, select OpenSSH Client, and click “Install”.
For Windows 10 & 11
- Press the Windows key or open up the Start Menu. Type “cmd”.
- Under “Best Match”, click “Command Prompt”.
- In the command prompt, use the ssh-keygen command:
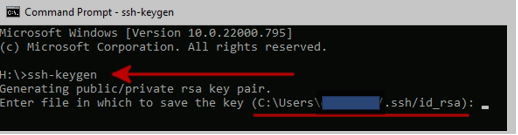
- By default, the system will save the keys to [your home directory]/.ssh/id_rsa. Unless you are an expert you should use the default option and press Enter.
- The system will now generate the key pair and display the key fingerprint and a random art image. These fingerprints are not needed in day-to-day use of your keys but can be saved to your notes to identify your keys later if needed.
- Open your file explorer. You can now navigate to the hidden “.ssh” directory in your home folder. You should see two new files. The identification is saved in the id_rsa file and the public key is labeled id_rsa.pub. This is your SSH key pair. They are both saved in plain text.
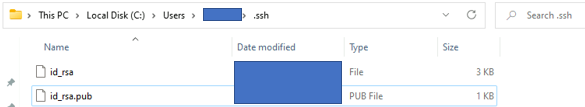
Generating SSH keys with PuTTY
- PuTTY is Free and Open Source software. It can be obtained from the PuTTY latest release page.
- Once PuTTY is installed, press the Windows key, or open the Windows and type “puttygen” and open the “PuTTYgen” app.
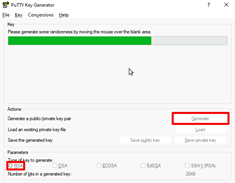
- In the PuTTY Generator window, make sure that “RSA” is selected at the bottom of the window and click “Generate”. Move your mouse cursor over the gray area to fill the green bar.
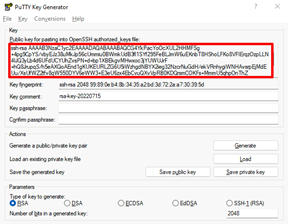
- You need the public key written at the top of the window for your authorized_keys file (see “Copying your public key to a host” below). PuTTY does not save the public key for you. You can copy and paste it directly to your authorized_keys file or copy and paste this key into a notepad document for safe keeping to copy later.
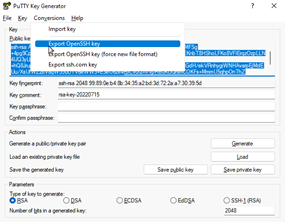
- Now the private key needs to be saved. Click the “conversions” menu at the top and select “Export OpenSSH Key”. Generally you want to save this without a passphrase, so click “Yes” in the next dialog box. Choose a location to save the key and give your key a name (e.g. putty_key).
- Your keys are generated and you can close the PuTTY key generator. To use your new key with PuTTY, you need open “Connection” and “Auth” in the PuTTY configuration. Under “Private Key file for authentication” choose the private key you just saved.
Copying your public key to a host
Public keys are in text format and copying them to a remote host can be done with cut and paste commands. The public key file you created can be opened with a text editor and it will look something like this:
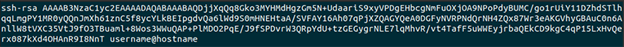
The key can contain numbers, letters, or symbols like the one above. On remote Unix, Linux, or MacOS machines the public key needs to be placed into a file called ~/.ssh/authorized_keys file* using your favorite text editor. There can be multiple public keys in the authorized_keys file. If the file does not exist it needs to be created. Your authorized_keys file needs to be set to owner read/write only (mode 600).
*If the authorized_keys file or the .ssh folder is not present:
- to confirm the missing .ssh folder run: ls -la ~/
- to create the folder: mkdir ~/.ssh
- change the permissions of the folder: chmod 700 ~/.ssh
- create the authorized_keys file: touch ~/.ssh/authorized_keys
- change the permissions of the file: chmod 600 ~/.ssh/authorized_keys
Creating and Using SSH Keys in Mac and Linux
Generate a SSH Key Pair
- Open a new Terminal window
- Type ssh-keygen -b 4096 -t rsa
- You will be prompted to enter a filename. By default, your keys will be saved as id_rsa and id_rsa.pub. Simply press Enter to confirm the default – there is no need to change this unless you have multiple keys. (Note: if you would like to change the default filename, you’ll need to include the complete file path)
- When prompted, enter a passphrase.
- This will created a hidden directory called .ssh that contains both your public (id_rsa.pub) and private (id_rsa.) key files.
View your public key
- In the same Terminal window, type cat .ssh/id_rsa.pub. This will print your public key
Copying your public key to a host
Public keys are in text format and copying them to a remote host can be done with cut and paste commands. The public key file you created can be opened with a text editor and it will look something like this *:

The key can contain numbers, letters, or symbols like the one above. On remote Unix, Linux, or MacOS machines the public key needs to be placed into a file called ~/.ssh/authorized_keys file using your favorite text editor. There can be multiple public keys in the authorized_keys file. If the file does not exist it needs to be created. Your authorized_keys file needs to be set to owner read/write only (mode 600).
Multi-Hop Steps
Command
This command is used to create an SSH (Secure Shell) tunnel:
ssh -f user@host -L port:localhost:port-N
Breakdown
- ssh: This is the basic command used to start an SSH client program that will connect to host.
- -f: This option tells SSH to go into the background just before it executes the command. This is useful for creating tunnels.
- user@host: This part specifies the SSH user and host you are connecting to. Replace user with your username on the remote machine and host with the domain name or IP address of the remote machine.
- -L port:localhost:port: This is the option for port forwarding. It tells SSH to listen to the first port on your local machine, forward all traffic that it receives on this port to localhost:port on the remote side. This is a way to securely tunnel network connections.
- The first port is the local port on your machine.
- localhost refers to the remote machine in the context of the SSH session.
- The second port is the port on the remote machine that you’re forwarding traffic to.
- -N: This tells SSH that no remote commands will be executed and is useful for just forwarding ports.
This command is what is used to often securely forward traffic from one machine to another, or to access a service on a remote machine securely. The SSH tunnel encrypts your data which helps protect your information over the network.
Example
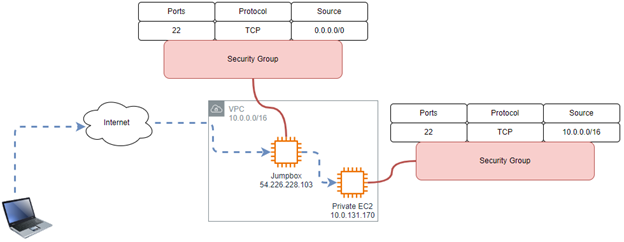
- Jumpbox has an IP address of 54.226.228.103 and listening on the standard SSH port 22
- We want to create an SSH tunnel to access another machine with the IP 10.0.131.170 (also on port 22), which allows SSH traffic from the jump box
Command
ssh -f user@54.226.228.103 -L 5000:10.0.131.170:22 -N
Breakdown
- user: This should be your username on the remote host 54.226.228.103, which you copied the public key for.
- 54.226.228.103: This is the IP address of the remote host where your SSH session will connect to.
- -L local_port:10.0.131.170:22: This option sets up the port forwarding.
- local_port: This is a port number on your local machine. You can choose any available port (commonly in the range 1024-65535). In this example, let’s say you choose 5000.
- 10.0.131.170: This is the IP address of the machine you want to tunnel to.
- 22: This is the port you’re targeting on 10.0.131.170, which in this case is the SSH port.
Final Steps
After running the above command, open up a new terminal and now you can SSH into 10.0.131.170 via port 5000 on your local machine and login with the password to the remote host:
ssh user@localhost -p 5000
Conclusion
SSH multi-hopping is a powerful technique for network administrators and those needing secure access through multiple network layers. However, it requires careful planning and understanding of the network architecture to implement effectively.